Understanding SCIM and its Importance in User Provisioning
Understanding SCIM and its Importance in User Provisioning
Organizations work with different vendors and applications to fulfill different needs. From HRMS to Payroll and finance, organizations use a multitude of applications. Imagine onboarding a new client with hundreds of employees who need access to all these different applications, with each employee requiring specific permission based on their role.
Keeping up with this manually is a nightmare for IT admins. As organizations expand, managing user identities across these applications becomes difficult. Changes in roles, departments, and departures require manual updates, which leads to delays, inconsistencies, and potential security gaps.
This is where tools like SCIM—System for Cross-domain Identity Management—come in handy. These tools automate these processes and ensure activities like provisioning and de-provisioning happen seamlessly, thus reducing the burden on IT teams and improving their efficiency.
In this post, we’ll explore SCIM in depth, explaining how it solves these B2B identity management challenges and why it’s essential for organizations operating in the B2B SaaS space.
Issues With SCIM Identity Management
With tons of SaaS applications in the current B2B landscape, managing user identities is challenging. These challenges affect business operations and lead to security loopholes in the organization.
Let us look at some common identity management issues.
Inefficiencies in Managing Identities Across Multiple Platforms
When a new employee joins the organization, their details need to be entered into multiple systems like HRMS, email, and CRM platforms based on their role. Doing this manually is time-consuming, leading to data inconsistency, misaligned access control, and workflow disruptions over time.
Administrative Overload and Risk of Human Errors
The manual process of updating user details in the system for every employee onboarding and deboarding is prone to human errors. Not adding the right permissions when a new user is added to the system or not revoking the permissions after the user is removed can lead to significant security risks.
Delays in Onboarding and Offboarding Processes
Delays in new user onboarding can affect the productivity of that person and the entire team. When new hires are not granted immediate access to the necessary tools, it disrupts workflows and adversely affects their productivity. Similarly, slow offboarding can lead to significant security risks. When former employees retain access after offboarding, it poses a significant risk.
Challenges in Maintaining Security and Access Controls
Ensuring that the right people have the right access is always a challenge. People change roles in the organization, so their access to resources is dynamic. Without a centralized system, maintaining strict access controls becomes difficult, increasing the likelihood of unauthorized access.
Hidden Costs and Inefficiencies in Identity Management
All the time and resources spent manually managing identities are significant. Inefficiencies in identity management waste time and lead to unnecessary operational costs. IT teams might spend several hours each week managing user accounts across various systems, diverting resources from more strategic IT initiatives.
These were some of the common challenges and complexities of identity management in B2B scenarios that can lead to operational inefficiencies, security risks, and increased costs. SCIM is designed to counter all these issues.
What is SCIM?
SCIM, or System for Cross-domain Identity Management, is an open standard that defines and standardizes automated user provisioning and de-provisioning across different systems. It is built on an object model where a Resource is the common denominator, and all SCIM objects are derived from it. It provides an HTTP-based protocol and schema, making managing identities in multi-domain scenarios easier.
Originally dubbed - simple cloud identity management, the first version of SCIM was introduced in 2011 by the Open Web Foundation. The second version was released in 2015, and since then, it has been widely adopted. It emerged from a collaboration between industry leaders like Cisco, Google, and Salesforce, who wanted a new, less complex standard that cloud service providers would easily adopt.
Simplifying SCIM
Let us understand each element of SCIM and how it contributes to its functioning and identity management.
- S - System: System refers to the interconnected software systems and applications for which SCIM provides a standardized way to communicate and manage user identities.
- C - Cross-domain: SCIM can work across domain names - internal tools, cloud providers, and third-party applications - and provide seamless identity management.
- I - Identity: The core of SCIM is identity, which deals with user profiles, roles, and access permissions. SCIM standardizes how these are managed across different platforms.
- M - Management: SCIM automates the provisioning, updating, and de-provisioning of user identities and hence helps manage user identities easily.
Key Features
Let us explore some of the important features of SCIM and understand how they help you deal with user identities.
Standardized User Data Format
One of SCIM's most important features is the standardization of user data format. It uses a standardized scheme to represent user attributes like username, email, and roles. For example, when adding a new user to your HRMS application, SCIM ensures that the user’s data is consistent across other systems like Google Workspace, Slack, etc., eliminating the need for custom integrations.
Automated User Provisioning and De-Provisioning
SCIM automates user creation, updating, and deletion across multiple platforms. This eliminates human intervention and reduces discrepancies. For instance, when a new user is added to HRMS, SCIM can automatically add the user to AWS and GitHub with the correct permissions. Similarly, when the user leaves the organization, SCIM will remove the user across all platforms and revoke all their access.
Interoperability Across Systems
SCIM is designed to operate across different systems, and one of the enabling features is the standardized data format. A company using Google Workspace for identity management and Okta for SSO can leverage SCIM to sync user data between these systems. This interoperability reduces the complexity of managing user identities.
Enhances Security and Compliance
By automating user provisioning and de-provisioning, SCIM enhances security and compliance. When a user’s role changes, SCIM automatically updates their access across different systems like AWS and GitHub, ensuring compliance with specific standards like GDPR, HIPAA, or other regulations relevant to B2B organizations.
SCIM Components
SCIM’s ability to simplify, automate, and streamline user identity management is based on well-defined protocols, schemas, and APIs. These components are the building blocks that allow SCIM to securely and efficiently manage user data across different systems. Let’s explore SCIM components and understand how they operate.
SCIM Protocol
This is an application-level protocol designed to standardize how user identity and associated information is shared between different systems. It defines how user data should be created, updated, synchronized, and deleted across different platforms. It uses REST API for exchanging this information, making it compatible with a wide range of systems. So when a new user is onboarded to HRMS, SCIM protocol defines how the profile is created and synchronized across other systems like Slack, Jira etc.
SCIM Specification
Two key RFCs define the SCIM specification:
- RFC7643: This defines the core SCIM schema for the structure of users and groups. It lists the attributes that can be part of a resource. For example, a `user` resource must have a unique username along with a title, email address, groups, and other attributes. Read more about RFC7643 to learn more.
- RFC7644: This RFC specifies how CRUD operations should be performed using RESTful APIs. It includes HTTP methods like POST, GET, PUT, PATCH, and DELETE to manage user identities. Read more about RFC7644 to learn more.
SCIM Schema
The SCIM schema defines the structure of user and group resources, defining how attributes like usernames, emails, and group memberships are represented. The schema provides a standardized way to describe these attributes. It is extensible, allowing organizations to add custom attributes specific to their needs while maintaining compatibility with different systems.
Commonly Used SCIM Schema Attributes and Objects
- User Object: This includes attributes like `userName`, `name`, `emails`, `phone numbers`, and `roles`.
- Group Object: Includes attributes like `displayName` and `members`. The members attribute typically contains a list of users who belong to the group.
- Enterprise User Schema: This schema extends the core user schema with additional attributes like `employeeNumber`, `costCenter`, and `organization`.

SCIM Endpoints
These are the URLs at the SCIM-compliant service provider’s end where requests are sent. These endpoints handle all requests for creating, updating, and deleting user accounts. All service providers expose specific endpoints for specific tasks following the SCIM protocol. These are RESTful API endpoints that manage identity resources like users and groups.
Common SCIM Endpoints and Their Functions
- /Users: Manages user resources, including creating, updating, retrieving, and deleting user accounts.
- /Groups: Manages group resources, including adding or removing users from groups.
- /Schemas: Provides information about the supported SCIM schemas and custom extensions.
SCIM also provides the following discoverability endpoints to discover supported features and specific attribute details and improve interoperability:
- GET /ServiceProviderConfig: Discover the Specification compliance, authentication schemes, and data models.
- GET /ResourceTypes: An endpoint used to discover the types of resources available.
- GET /Schemas: Endpoint to introspect resources and attribute extensions.
SCIM APIs and Tokens
SCIM APIs are critical for enabling seamless identity synchronization across multiple systems. These RESTful APS facilitate creating, updating, and deleting identities and associated attributes across multiple systems. SCIM APIs are based on the SCIM protocol and standardize how identity information is managed across systems.
These APIs enable identity providers to exchange identity information with service providers for various identity-associated tasks. They also simplify integrating different systems and automate user provisioning and de-provisioning activities. Thus, these APIs provide a consistent interface for managing user identities across multiple systems.
For example, when a new user is onboarded to Google Workspace, a SCIM API call can be made to multiple service providers simultaneously to ensure their accounts are set up correctly on all systems.
Some of the commonly used SCIM APIs:
- Create: POST https://example.com/{v}/{resource}
- Read: GET https://example.com/{v}/{resource}/{id}
- Replace: PUT https://example.com/{v}/{resource}/{id}
- Delete: DELETE https://example.com/{v}/{resource}/{id}
- Update: PATCH https://example.com/{v}/{resource}/{id}
SCIM Tokens
SCIM tokens authenticate and authorize SCIM API requests between identity providers and service providers. A SCIM access token is typically a JSON Web Token (JWT) with the necessary permissions to perform specific SCIM operations.
Unlike other tokens, SCIM tokens are specifically scoped for identity management operations. Let us look at how they are different from regular access tokens.
SCIM Provisioning
SCIM provisioning is the automated process that creates, synchronizes, and deletes users and associated data across multiple systems. Based on standardized protocols for data exchange, it ensures consistency in user identities across different systems. Before we understand the SCIM provisioning process in detail, let’s look at the components of
SCIM provisioning works by leveraging RESTful APIs that allow identity providers (IdPs) to communicate with service providers (SPs). When a new hire being onboarded and added to the identity provider’s end, SCIM triggers API calls to create or update the user’s account on connected service providers. Similarly, when a user leaves the organization, SCIM automates the deactivation or deletion of their accounts across all integrated systems, ensuring access is promptly revoked.
Key Components Involved in SCIM Provisioning
- Identity Provider (IdP): The system that manages user identities, such as Azure AD, Okta, or Google Identity.
- Service Provider (SP): The application where user accounts are provisioned, such as Salesforce, Slack, or AWS.
- SCIM Server: The endpoint on the service provider’s side that receives and processes provisioning requests.
- SCIM Client: This client is part of the identity provider and sends SCIM requests to the service provider to manage user accounts.
SCIM Connectors
A SCIM connector is an intermediary between the SCIM-compliant identity provider and the service provider, translating SCIM requests and responses into actions that can be performed on the target system. For example, a SCIM connector for Workday would take an SCIM request to create a user and translate it into the necessary API calls to create the user within Workday.
SCIM connectors are critical for integrating different systems with SCIM to ensure that user provisioning and de-provisioning happen correctly on target systems. Without SCIM connectors, organizations would have to build custom integrations for each system, making the process slow and prone to errors while adding an overhead of managing them.
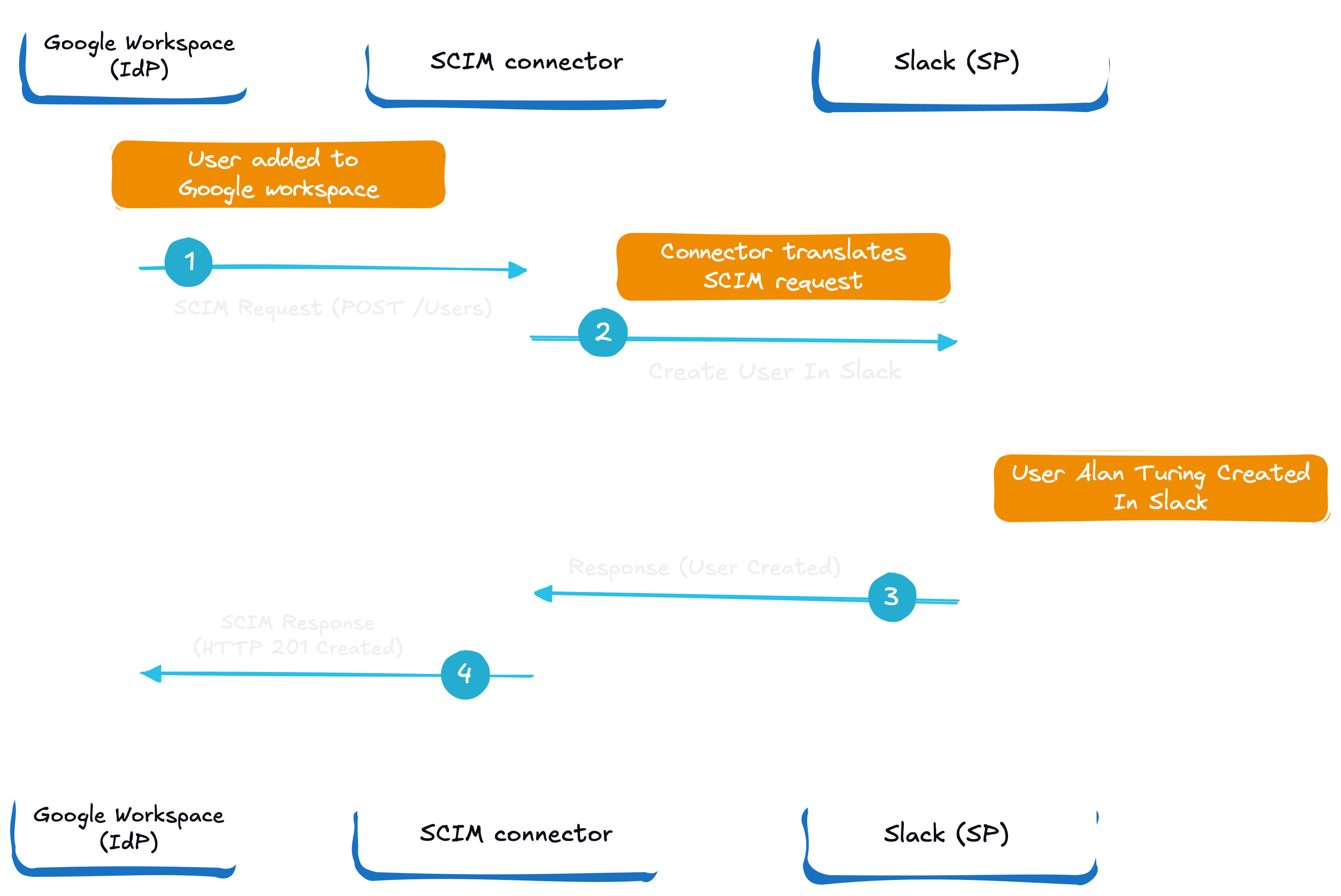
SCIM connectors receive SCIM requests from a SCIM-compliant identity provider, map the SCIM attributes to the corresponding fields in the target system, and then execute the necessary API calls to perform the requested actions. For example, when a new user is added to HRMS, the SCIM connector translates the request and creates the user in GitHub with the appropriate attributes.
How SCIM Provisioning Works
SCIM provisioning works by making API calls to the SCIM endpoints for performing various tasks:
- User Creation: When a new user is added to the IdP, the SCIM client sends a POST request to the SCIM server on the SP’s side to create the user account.
- User Updates: Any changes to a user's profile, such as a role change, trigger a PATCH request to update the user’s information across all integrated SPs.
- User Deletion: When a user is deactivated or removed from the IdP, a DELETE request is sent to the SCIM server to remove the user’s account from the SPs.
SCIM Provisioning Example For B2B SaaS Applications
Let's understand SCIM provisioning with an example. When a new employee joins a company, their user account must be provisioned across multiple platforms, such as Google Workspace, HRMS, GitHub, and other internal tools. SCIM streamlines this process by automating user account creation, update, and deactivation.
The first step is to add the user to the identity provider, in this case, Google Workspace. This triggers an internal SCIM client in Google Workspace to begin provisioning the user across connected systems.
Below is a sample User resource:
Google Workspace, acting as the SCIM client, sends POST requests to the SCIM servers of HRMS and GitHub to create the user accounts there. Below is how a sample POST request would look like
The HRMS, GitHub SCIM server receives the POST request and provisions Alan Turing's user account. Below is a sample HTTP 201 response for the above request.

Implement SCIM Provisioning in Your Organization
Implementing SCIM in your organization can greatly improve your identity management process and make the process seamless and efficient. While we understood the concepts and workings of SCIM, implementing it requires careful planning and execution. In this section, we’ll list the steps you must follow to implement SCIM in your organization.
1. Assess Your Identity Management Needs
The first and foremost question you should ask yourself is, “Do you really need SCIM?” Understanding your organization’s needs and challenges regarding identity management is crucial. Evaluate your current workflows for creating, updating, and deleting user identities and identify the gaps and inefficiencies that SCIM can address.
2. Choose the Right SCIM Solution
Once you’ve identified your needs, select a SCIM offering that aligns with your organization’s identity management needs. Consider factors such as integration and compatibility with your existing systems, ease of integration, and support for SCIM protocols. The solution you choose must simplify your identity management processes without causing disruption.
3. Integration with Existing Systems
Integration is key to a successful SCIM implementation. Ensure that your chosen SCIM solution integrates seamlessly with your current identity provider, HR systems, and other critical applications. Pay special attention to how SCIM connectors and endpoints are configured to ensure smooth communication between systems.
4. Best Practices for Smooth Implementation
Follow the best practices for implementing SCIM for a foolproof implementation. Start with a test phase where you set up SCIM, integrate it with a small set of tools, and roll it out to a subset of users before deploying it organization-wide. Involve all the key stakeholders in the planning process throughout implementation and ensure everything is documented and training is provided to all relevant stakeholders.
5. Monitoring and Maintaining SCIM Deployments
After implementing a SCIM solution, it's crucial to monitor it continuously. Validate the synchronization between systems, audit access controls, and update configurations as needed. Monitoring tools can help you track the performance and health of your SCIM deployment and warn you of any vulnerabilities that can cause a disruption.
Advantages Of Using SCIM
SCIM offers numerous advantages that can transform your complex and time-consuming identity management process. Here are some of the advantages:
Streamlined Identity Management Processes
Using a standard schema, SCIM provides a standardized way to automate the provisioning and deprovisioning of user accounts across different services and applications. This also ensures that user identities are consistent across systems, eliminating the need for manual intervention. Whenever a new user is onboarded into the identity management system, SCIM automatically creates corresponding accounts for different services like Slack, GitHub, etc.
Reduced Administrative Burden and Human Errors
SCIM eliminates manual intervention in the identity management workflow. The automated process not only reduces manual intervention but also minimizes the chances of human errors, such as forgetting to revoke access when a user leaves the organization or assigning incorrect/insufficient permissions to a new hire that affects their productivity.
Faster Onboarding and Offboarding
Onboarding and offboarding-related activities are accelerated with SCIM as the entire user provisioning and deprovisioning process is automated. This is beneficial for fast-growing organizations where rapid onboarding is critical. Further, SCIM-enabled systems can provision all necessary accounts within minutes of a new employee’s hire, ensuring immediate access to the tools they need.
Improved Security and Access Control
Apart from automating identity management processes, SCIM ensures that a user’s access is tightly controlled and enforced across all systems. It supports role-based access control (RBAC) and attribute-based access control (ABAC), allowing organizations to control fine-grained permissions. This ensures that all the users have only the required access and permissions that they are supposed to, thus enhancing overall security.
Cost Savings and Efficiency Improvements
SCIM helps organizations reduce operational costs and overheads by automating identity management processes. The time and resources saved on manual processes allow teams to focus on more critical tasks, thus improving overall efficiency. Further, SCIM’s ability to manage user access reduces the cost of potential security breaches, which can be costly.
Common Use Cases of SCIM
Whether integrating with SaaS applications, synchronizing HR systems, or enhancing enterprise access management, SCIM provides a standardized approach to managing user identities efficiently and securely.
In this section, we’ll explore some of SCIM's most common use cases and highlight how you can use it to address specific B2B identity management challenges in your organization.
Enterprise Applications and SaaS Integrations
SCIM makes it easier for B2B organizations to integrate with 3rd-party service providers by automating user provisioning and de-provisioning. For instance, when an organization adopts a new SaaS tool, SCIM can automatically create user accounts, assign roles, and sync other information to the new tool. This ensures that employees have immediate access to the new tool and that this entire process is free of manual intervention.
HR Systems and User Directory Synchronization
Employees join, leave, or change roles within an organization - this is SCIM’s most impactful use case. SCIM can ensure all these changes are updated and synchronized across all connected systems. For instance, when a user is promoted in the HRMS, their permissions will be updated in all the other applications based on their new role.
Access Management and Single Sign-On (SSO)
SCIM can help with role and enterprise access management when implementing Single Sign-On. Using SCIM, organizations can automate the management of user identities and roles across multiple systems, ensuring that users have the correct permissions based on their roles.
Identity Governance and Compliance
SCIM enhances governance and compliance by providing a standardized way to manage user identities and access controls. This is important for organizations that must comply with GDPR, HIPAA, or other industry regulations. SCIM ensures that access rights are accurately assigned and updated in real-time, reducing risk on non compliance.
Best Practices and Challenges of SCIM
We discussed the process of implementing SCIM in your organization and its benefits. However, every technology has its own challenges. In this section, we look at some of the best practices and challenges associated with SCIM.
Best Practices
- Start with a Pilot Deployment: Before rolling out SCIM across your entire organization, begin with a pilot project. Roll it out to a subset of users, integrate it with some of your tools, and see how it works. This allows you to identify potential issues and fine-tune configurations in a controlled environment.
- Regularly Monitor and Audit SCIM Integrations: Continuously monitor SCIM integrations to ensure they function as expected. Regular audits can help detect discrepancies in user data or access permissions across multiple systems, allowing for timely corrections.
- Data Privacy and Security: Enforce authentication mechanisms, such as OAuth, for SCIM API access and ensure data is encrypted. Regularly review and update security policies to align with current best practices and compliance requirements.
- Optimize Attribute Mapping: Ensure that user attributes are mapped correctly between systems and that user data is consistent and compatible across different platforms. Simplify attribute mappings where possible and use standardized attributes defined by the SCIM specification to reduce complexity and potential errors.
- Implement Role-Based Access Control (RBAC): Use SCIM to enforce RBAC policies across your integrated systems. This ensures that users have the appropriate level of access based on their roles, reducing the risk of unauthorized access.
Challenges
- Inconsistent Data Across Systems: Inconsistent data across systems can disrupt identity management workflows and user provisioning. To address this, it’s crucial to establish clear data governance policies and regularly synchronize user data between systems. Automated validation checks must be implemented to catch and resolve discrepancies early, ensuring data remains consistent across all systems.
- Integration with Legacy Systems: Integrating SCIM with legacy systems can be challenging as there is often no out-of-the-box solution. Organizations can utilize SCIM connectors that act as a bridge between SCIM and older systems. In cases where standard solutions aren’t available, custom connectors can be developed to ensure seamless integration.
- Handling Role and Permission Conflicts: Role and permission conflicts can lead to unauthorized access or operational inefficiencies. Implementing a centralized role management system that defines clear role hierarchies and access levels is essential. Regular audits help identify and resolve such issues.
- Managing API Rate Limits and Performance: API rate limits can hinder the performance of SCIM integrations, especially in large-scale deployments. To manage this, organizations can optimize SCIM API calls by batching requests or using incremental updates to reduce system load. Implementing caching mechanisms can also enhance performance and decrease the frequency of API calls, ensuring smoother and more efficient operations.
- Keeping Up with Evolving SCIM Standards: As SCIM standards evolve, it's important to stay informed and ensure your implementation remains compliant. It's crucial to regularly review and update your SCIM setup in accordance with the latest standards and best practices.
Summary of SCIM
SCIM is a critical solution for identity management in modern systems. It provides an automated solution for managing user identities, enhancing security, and improving efficiency. By addressing the challenges of data inconsistency due to manual errors, SCIM ensures that organizations can manage identities efficiently.
As the demand for seamless identity management grows, SCIM is set to play a pivotal role in organizations. With the rise of cloud computing, there’s a need for robust identity management and access control, and SCIM can easily address these.
For any organization wanting to improve its identity management processes, adopting SCIM can do wonders.




